Tuesday, September 22, 2020
Ep 31: No School Like The Old School Is Live!
Monday, September 21, 2020
Camouflaging The Imperial Guard Armoured Company
Not many updates but I've been slogging through the camouflage on the Armoured Company these past weeks. The base colors and shading are done, I'm now onto tidying. That should finish up this week and hopefully I can start on the highlights.

The green and tan each get a base, wash, neaten up, and two highlights. The black and metal get a wash and a highlight or two, depending on how they look.



I also painted this guy up over the course of a couple hours this week. He's a battle wizard from my last Kickstarter. He's meant to be a gold wizard/alchemist.


Saturday, September 12, 2020
Game 378: Goodcode's Cavern (1982) And Romero/Carmack Corrections
Gebelli Software (publisher)
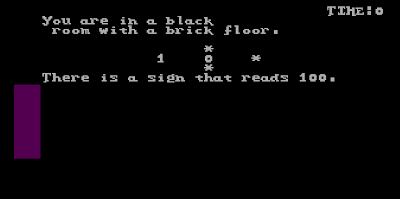 |
| Stepping into the first room. |
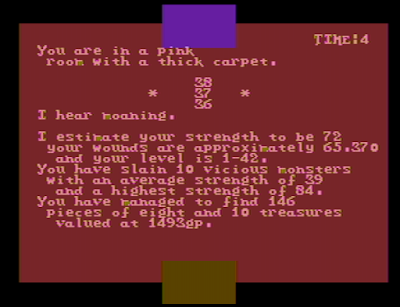 |
| This room is pink with a thick carpet and there's moaning. |
 |
| Hot tacos indeed. Although I suspect if I saw a blue grizzly bear, I'd start blaming something else I got in Mexico. |
 |
| Finding a "nickel headband" and then checking my status. |
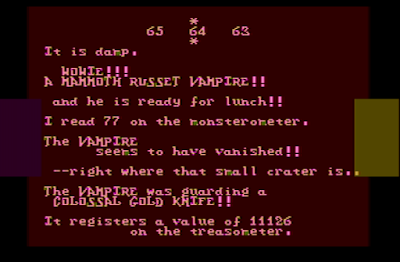 |
| The mammoth russet vampire was a little too much for me, so I zapped him with the wand. I'm glad I did, because the colossal gold knife was worth a lot of money. |
 |
| A demon convinces me to pay reparations. |
 |
| No, but you can resurrect me. |
 |
| Room 80 on Level 1. |
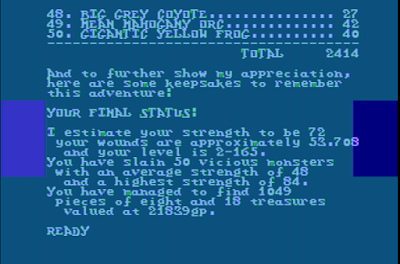 |
| The winning screens. |
 |
| I have no idea what's happening here. |
1991 was a major transition year for Carmack and his new partner, John Romero. At the age of 20, Carmack had gotten a job two years prior at Softdisk, largely on the strength of his Dark Designs series. But he and the other developers grew to despise the sweatshop-like atmosphere of Softdisk and the monthly programming demands. He and Romero began moonlighting by selling their own games--principally the Commander Keen series--as shareware on bulletin board services. When Softdisk found out about these games, and that the pair had been using the company's computers to write them, both threats of a lawsuit and offers of a contract followed. The messy result was that Carmack and Romero left the company but agreed to continue to produce one game every 2 months for Softdisk's magazines. Thus, a couple years later, after the team had changed the gaming world forever with Wolfenstein 3D and DOOM, you see them credited on the occasional diskmag title like Cyberchess and Dangerous Dave Goes Nutz!
- I was a year late; 1990 was the year most of this happened. Romero worked at Softdisk prior to Carmack and was actually the one who hired Carmack, not because of Dark Designs but because of a tennis game plus his obvious facility with programming.
- Romero and Carmack loved working at Softdisk and only left because it was the wrong sort of publisher to take advantage of the horizontal scrolling technology that the duo would use in Wolfenstein 3D and DOOM.
- It was actually the president of Softdisk, Al Vekovius, who suggested that Carmack, Romero, and Tom Hall start their own company. There were no lawsuits and no threats; Carmack and Romero kept working for Softdisk for a year to avoid leaving the company in a lurch.
- The reason Carmack and Romero are credited on so many Softdisk titles stretching into the mid-1990s is that those titles used technology and code that Carmack and Romero had created. They otherwise had no involvement in games like Cyberchess and Dangerous Dave Goes Nutz!
Sister Tempest By Joe Badon, Movie Review
Anne Hutchinson promised Karen, her younger sister, when they were orphaned that she would take care of her and always be with her till the day they died. As they grew up, Anne worked hard to be the parent she knew Karen needed. They grew older and grew apart as Karen developed a relationship with a young man. He had his problems and Anne didn't like him or what it would mean for Karen. They argued and Karen left, vowing to never return. That night Karen's boyfriend was murdered and Karen was missing.
That is the starting premise of Sister Tempest,which is written and directed by Joe Badon (IMDb link). What happens after is a rollercoaster ride through Anne's psyche. As she deals with the trauma of her missing sister, her internal tempest swirls.
 |
The Story Side
Sister Tempest is summarized with the following.
"Anne Hutchinson's troubled relationship with her missing sister is under alien tribunal. Meanwhile, her new roommate's mysterious illness causes her to go on a cannibalistic killing spree."
I'm not going to say much about the plot. The story constantly weaves back on itself with flashbacks and flash-forwards, along with jumps through dimensions, as Anne recites her tale of events to a panel of "judges." They want to know the story from her point of view so they can get to the truth as Anne perceives it. And, that is the real question as the story unfolds.
Badon tells his story of Anne in an art house style. Throughout the movie, scenes are cut into and out of to produce chapters set apart by short scenes giving foreshadowing to the events about to unfold. This is a film that needs to be watched carefully. The story seems rough and a little hard to follow at first. But, as the chapters unfold, the pieces of the puzzle of Anne's stormy mind settles.
 |
The Production Side
I first met Joe Badon at the FilmQuest Film Festival (website) when he was screening his first feature film, The God Inside My Ear(IMDb link). If you liked his first film, you will enjoy Sister Tempest. Both have the aspect(?) of mental self-discovery.
Badon provides a lot of little tidbits in his film. Along with the foreshadowing within the chapter headers, there are a number of symbols, metaphors, and tokens used to bring the story full circle from the opening scenes through the "flashback" telling of the story by Anne to the final scene of discovery. It is because of these elements woven into the plot that it would be unfair to give an outline without giving away the end.
Sister Tempest is a low budget film. Instead of detracting from the film, if allowed, the level of technical special effects adds to the story. We are being told the story through Anne's viewpoint, her perception of events, her reality, which is not a good place. The special effects are reminiscent of older movies and Sister Tempest includes scenes from sci-fi, horror, and other classic films. Many times when people think of low budget, they think there isn't much talent involved. That is not the case.
The cast of Sister Tempest has a broad range of experience. The combination of talent provides depth for the style and budget. Two of the main roles are Anne and her new roommate after Karen leaves, Ginger.
Anne Hutchinson is played by Kali Russell (IMDb link). This is her second listed credit and her first feature film. Her portrayal of Anne gives us a woman facing a breakdown. Everything she has worked to maintain in her life for her and her sister is gone. The sense of loss is palpable. She brings this out in her dealings with the events of her daily routine and when dealing with new possibilities and other characters. For a first major role, I like what Kali Russell brings to the story and to the screen.
Ginger is portrayed by Linnea Gregg (IMDb link), who is returning to work with Joe Badon after playing the lead role of Elizia in The God Inside My Ear. She also brings an insight to the mental stresses taking place and how they are dealt with. She provides an excellent counterpoint to Russell's Anne. They show their connection to each other on screen and allow the story to grow.
Sister Tempest is prepared to be on the film festival circuit. At the time of this review, there was no mention of where Sister Tempest will be screened.
I recommend Sister Tempest for people who want to see a film that is different, thought provoking, and requires you to pay attention to what is happening on the screen.
You can find out more about Sister Tempest on IMDb (IMDb link).

I'm working at keeping my material free of subscription charges by supplementing costs by being an Amazon Associate and having advertising appear. I earn a fee when people make purchases of qualified products from Amazon when they enter the site from a link on Guild Master Gaming and when people click on an ad. If you do either, thank you.
If you have a comment, suggestion, or critique please leave a comment here or send an email to guildmastergaming@gmail.com.
I have articles being published by others and you can find most of them on Guild Master Gaming on Facebookand Twitter(@GuildMstrGmng).
Thursday, September 3, 2020
Monthly Progress Report For My Twitch Channel, FuzzyJCats, Nov 25 Through Dec 24
During this month of streaming, I continued to work on improving the usual chatting and gaming at the same time, and not using filler words, though I noticed I constantly slip into using a lot of filler words as they help to fill dead air.
I was also trying to find out how we can tell if we're entertaining. Certainly watching your VoDs help you notice if you're articulate or not, if you move around too much such that you're off the facecam, but I still can't tell if my streams are entertaining.
However, I started having an inkling as to what's entertaining to viewers this month. Since the entertainment is in real-time, and people are chatting, like with everything, people find you very interesting if you ask about them and talk about their issues. This is try-hard but cbenni.com can let you review your logs so you can remember what your viewers say, so when they show up the next time, you can ask them about that specific thing.
For instance, if they mention that they're starting a new job, you can ask them how work is coming along, if they like their new boss, coworkers, and so on and so forth.
So another try-hard method is after each stream, I have been more or less writing these topics to talk about when the viewer shows up next.
Again, this is very try-hard, but it can help not only make your chat more entertaining for specific viewers, but with these topics on hand, it will help reduce dead air.
Aside from the usual goal of chat and gaming ratio, working on dead air, and removing filler words while streaming, improvements to be made is to be more aware of my viewers so I can ask them about issues next stream.
The How of Happiness Review
Sunday, August 30, 2020
CSRF Referer Header Strip
Intro
A couple months ago I had to deal with an application that was checking the Referer as a CSRF prevention mechanism, but when this header was stripped from the request, the CSRF PoC worked. BTW it is common practice to accept empty Referer, mainly to avoid breaking functionality.
Solutions for Referer header strip
- learn something very cool;
- have a serious headache from all the new info at the end.
Rich Lundeen (aka WebstersProdigy) made an excellent blog post on stripping the Referer header (again, make sure you read that one first before you continue). The HTTPS to HTTP trick is probably the most well-known one, general and easy enough, but it quickly fails the moment you have an application that only runs over HTTPS (this was my case).
The data method is not browser independent but the about:blank trick works well for some simple requests. Unfortunately, in my case the request I had to attack with CSRF was too complex and I wanted to use XMLHttpRequest. He mentions that in theory, there is anonymous flag for CORS, but he could not get it work. I also tried it, but... it did not work for me either.
Krzysztof Kotowicz also wrote a blog post on Referer strip, coming to similar conclusions as Rich Lundeen, mostly using the data method.
Finally, I bumped into Johannes Ullrich's ISC diary on Referer header and that led to me W3C's Referrer Policy. So just to make a dumb little PoC and show that relying on Referer is a not a good idea, you can simply use the "referrer" meta tag (yes, that is two "r"-s there).
The PoC would look something like this:
<html>
<meta name="referrer" content="never">
<body>
<form action="https://vistimsite.com/function" method="POST">
<input type="hidden" name="param1" value="1" />
<input type="hidden" name="param2" value="2" />
...
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
Conclusion
Related articles
- Nsa Hack Tools Download
- How To Hack
- How To Make Hacking Tools
- Hack Tools For Games
- Pentest Tools Open Source
- Hack Tool Apk No Root
- How To Install Pentest Tools In Ubuntu
- Top Pentest Tools
- Hacker Tool Kit
- Hack Tools Github
- Bluetooth Hacking Tools Kali
- Pentest Tools Url Fuzzer
- Pentest Tools Alternative
- Hacker Tools Software
- Hacks And Tools
- How To Install Pentest Tools In Ubuntu
- Pentest Tools Nmap
- Hacker Tools Apk
- Hack Tools For Windows
- Hacker Tools Software
- Pentest Tools Download
- Nsa Hack Tools
- Nsa Hacker Tools
- Underground Hacker Sites
- Hacker Tools Hardware
- Hackers Toolbox
- Pentest Tools Github
- Pentest Tools Find Subdomains
- Pentest Tools Online
- New Hacker Tools
- Best Hacking Tools 2020
- Hackrf Tools
- Hacker Tools Free Download
- Hacking Tools 2020
- Hack Apps
- Computer Hacker
- Hacker Tools 2020
- Top Pentest Tools
- Hack Tools Mac
- Wifi Hacker Tools For Windows
- Hacking Tools Hardware
- Hack And Tools
- Hacker Tool Kit
- Computer Hacker
- What Are Hacking Tools
- Pentest Tools Url Fuzzer
- Tools 4 Hack
- Hack Tools For Ubuntu
- Best Hacking Tools 2020
- Hacker Tools Free
- Tools For Hacker
- Hacker Tools For Pc
- Pentest Tools Find Subdomains
- Pentest Tools Windows
- Hacker Tools Apk
- Usb Pentest Tools
- Android Hack Tools Github
- What Are Hacking Tools
- Hacker Search Tools
- Pentest Tools Open Source
- Hack Tools For Mac
$$$ Bug Bounty $$$
A bug bounty program, also called a vulnerability rewards program (VRP), is a crowdsourcing initiative that rewards individuals for discovering and reporting software bugs. Bug bounty programs are often initiated to supplement internal code audits and penetration tests as part of an organization's vulnerability management strategy.
Many software vendors and websites run bug bounty programs, paying out cash rewards to software security researchers and white hat hackers who report software vulnerabilities that have the potential to be exploited. Bug reports must document enough information for for the organization offering the bounty to be able to reproduce the vulnerability. Typically, payment amounts are commensurate with the size of the organization, the difficulty in hacking the system and how much impact on users a bug might have.
Mozilla paid out a $3,000 flat rate bounty for bugs that fit its criteria, while Facebook has given out as much as $20,000 for a single bug report. Google paid Chrome operating system bug reporters a combined $700,000 in 2012 and Microsoft paid UK researcher James Forshaw $100,000 for an attack vulnerability in Windows 8.1. In 2016, Apple announced rewards that max out at $200,000 for a flaw in the iOS secure boot firmware components and up to $50,000 for execution of arbitrary code with kernel privileges or unauthorized iCloud access.
While the use of ethical hackers to find bugs can be very effective, such programs can also be controversial. To limit potential risk, some organizations are offering closed bug bounty programs that require an invitation. Apple, for example, has limited bug bounty participation to few dozen researchers.
- Top Pentest Tools
- Hack Tools Download
- Tools 4 Hack
- Physical Pentest Tools
- Pentest Tools Apk
- Nsa Hack Tools
- How To Hack
- Game Hacking
- Hacking Tools Kit
- Hacking Tools Software
- Hack Tools For Mac
- Pentest Box Tools Download
- What Are Hacking Tools
- Hacker Tools For Windows
- Easy Hack Tools
- Hacking Tools For Games
- Hack Tools Online
- Hacker Tools 2020
- Hacking Tools Github
- Hack Tools Mac
- Pentest Reporting Tools
- Pentest Tools For Ubuntu
- Easy Hack Tools
- Pentest Tools For Ubuntu
- Tools 4 Hack
- Tools 4 Hack
- Hack Tools Download
- Computer Hacker
- Github Hacking Tools
- Hack Website Online Tool
- Game Hacking
- Pentest Box Tools Download
- Computer Hacker
- Pentest Automation Tools
- Pentest Tools Bluekeep
- Android Hack Tools Github
- Pentest Tools
- What Are Hacking Tools
- Pentest Reporting Tools
- Beginner Hacker Tools
- How To Make Hacking Tools
- Hacking Tools Kit
- Android Hack Tools Github
- Pentest Tools Subdomain
- Best Hacking Tools 2019
- Github Hacking Tools
- Hack Tools
- Pentest Tools Windows
- Best Hacking Tools 2019
- Hacking Tools 2020
- Top Pentest Tools
- Pentest Tools Kali Linux
- Hacker Tools Linux
- Pentest Tools Find Subdomains
- Nsa Hack Tools Download
- Pentest Tools Open Source
- Hack Tool Apk
- Best Hacking Tools 2020
- Pentest Tools Port Scanner
- Bluetooth Hacking Tools Kali
- How To Hack
- Pentest Tools Linux
- Hack Tools For Mac
- Hacking Tools Free Download
- New Hack Tools
- Beginner Hacker Tools
- Hack Tools Online
- Hack Rom Tools
- Pentest Tools Website Vulnerability
- New Hack Tools
- Pentest Tools Find Subdomains
- Physical Pentest Tools
- Hack And Tools
- Hack Tools Download
- Tools For Hacker
- Hack Tools
- Hacking Tools For Mac
- Pentest Tools List
- Growth Hacker Tools
- Hacking Tools Github
- Pentest Tools Port Scanner
- Pentest Tools For Windows
- How To Install Pentest Tools In Ubuntu
- Pentest Tools Open Source
- Usb Pentest Tools
Administración Remota De Servidores Desde Android
Sin embargo una shell linux, no es viable en el teclado de un teléfono incluso de un tablet, sobretodo porque hay que escribir muchos símbolos, por ejemplo el guión, y estos teclados están pensados más bien para texto.
Pues bien, de esta necesidad surgió la aplicación SSHControl:
SSHControl
Esta problematica la he solucionado a base de utilizar nevegadores y estructurar los outputs para no acumular excesiva información en la pantalla.
- Navegador de ficheros
- Navegador de procesos
- Navegador de conexiones
- Navegador de logs
- Navegador de drivers de kernel
Esto permite administrar múltiples servidores con un solo dedo :)
Controlar la seguridad de sus servidores ahora es bastante sencillo y ágil, por ejemplo con solo hacer un "tap" encima de un usuario, podemos ver sos procesos asociados, con hacer otro tap en un proceso podemos kilearlo, ver mas info etc ..
Con hacer un tap encima de una apliacción, vemos sus conexiónes, con un tap en una conexión podemos agregar una regla de filtrado en el firewall, etc ..
En la siguiente versión habilitaré la opción de "Custom Commnands", la cual es muy util,
cada administrador o usuario linux, tiene una serie de comandos que repite con mucha frecuencia,
bien pues esta opción permite pre-programar estos comandos habituales, de manera que puedes lanzarlos con un simple tap.
En el roadmap tengo pensadas nuevas funcionalidades muy útiles :)
Aqui os dejo algunas capturas de pantalla:




More information
- Hackrf Tools
- Physical Pentest Tools
- Nsa Hacker Tools
- Easy Hack Tools
- Black Hat Hacker Tools
- Hacking Tools And Software
- Hacker Tools
- Hack Tools
- Hacker Tools 2020
- Pentest Tools List
- Hacking Tools Pc
- Hacker Search Tools
- Computer Hacker
- Hacking Tools For Kali Linux
- Hack Tools For Pc
- Hacker Tools For Pc
- Hacker Tools Apk
- Hacking Tools Usb
- Wifi Hacker Tools For Windows
- Hacking Tools For Windows Free Download
- Nsa Hacker Tools
- Hacking Tools Usb
- Pentest Tools List
- Pentest Tools Linux
- Computer Hacker
- Hackrf Tools
- Hacker Techniques Tools And Incident Handling
- Hacker Tools Apk
- Tools For Hacker
- Pentest Tools Android
- Hack Tools
- Hacker Hardware Tools
- Hack Tools For Games
- Pentest Tools Free
- Hacking Tools And Software
- Beginner Hacker Tools
- Pentest Tools Apk
- Underground Hacker Sites
- Hacking Tools
- Hacker Tools Mac
- Best Pentesting Tools 2018
- Hacker Tools Apk
- Hack Tools 2019
- Hacks And Tools
- Hacker Tools Apk
- Growth Hacker Tools
- Growth Hacker Tools
- Pentest Tools Nmap
- Hacking Tools For Windows Free Download
- Hak5 Tools
- How To Install Pentest Tools In Ubuntu
- Pentest Tools Free
- Hacker Search Tools
- Hacking Tools For Kali Linux
- New Hack Tools
- How To Hack
- Pentest Tools Find Subdomains
- Hacking Tools Kit
- Hacking Tools For Pc
- Nsa Hacker Tools
- Black Hat Hacker Tools
- Pentest Box Tools Download
- Hacking Tools For Kali Linux
- Hacking Tools Name
- Hack And Tools
- Nsa Hack Tools Download
- Pentest Tools Windows
- Hacking Tools Github
- Hacking Tools Hardware
- Hak5 Tools
- Pentest Tools Framework
- Pentest Tools For Android
- Hacker Tools Hardware
- Hackrf Tools
- Best Hacking Tools 2020
- Pentest Tools Tcp Port Scanner
- Pentest Tools Nmap
- Hacker Tools Free Download
- Ethical Hacker Tools
- Hack Tools For Games
- Pentest Reporting Tools
- Hacker Tools Github
- Pentest Box Tools Download
- Blackhat Hacker Tools
- Hacker Search Tools
- Hack Tools 2019
- Pentest Tools Android
- Hack Tools Pc
- Pentest Tools Bluekeep
- New Hack Tools
- Hacking Tools For Windows 7
- Hacker
- Hack Tools Github
- Physical Pentest Tools
- Hack Tools For Windows
- Hack Tools Mac
- Termux Hacking Tools 2019
- Underground Hacker Sites
- Hacker Tools 2019
- Hacker Tools 2019
- Hacker Tool Kit
- Github Hacking Tools
- Pentest Tools Linux
- Hacking Tools 2019
- Computer Hacker
- Hacking Tools Hardware
- Best Hacking Tools 2020
- Hacking Tools Usb
- Top Pentest Tools
- Hacker Tools Github
- Hacker Tools Linux
- Hacking Tools For Games
- Hacking Tools Windows 10
- Pentest Tools Github
- Blackhat Hacker Tools
- Hacker Tools Apk Download
- Hacking Tools Hardware
- Free Pentest Tools For Windows
- Black Hat Hacker Tools
- Hacker Tools Linux
- Top Pentest Tools
- Pentest Tools For Mac
- Tools Used For Hacking
- Hacking Tools Name
- Pentest Recon Tools
- Hack Tools Mac
- World No 1 Hacker Software
- Android Hack Tools Github
- Hacking Tools Online
- Hackers Toolbox
- Tools For Hacker
- Hacking Tools Free Download
- Tools For Hacker
- Hacker Tools Hardware
- Hack Tools Github
- What Is Hacking Tools
- Physical Pentest Tools
- Hack Tools





